Process
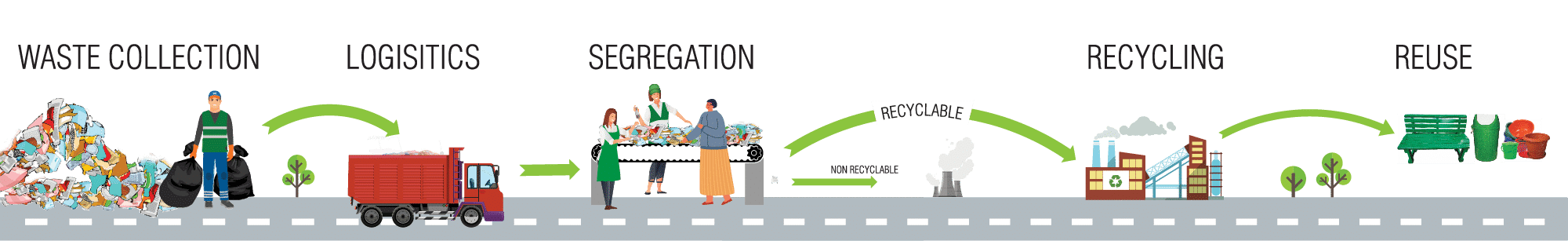
- Collect A collection agent is sent to the client’s premises to procure e-waste. Here the data destruction process begins. All the data is scrubbed either by degaussing or physical destruction before the e-waste leaves the client’s premises. After proper segregation, the material is approved for transportation.
- TransportThe closed container vehicle then carries out the transportation process from the client’s premises to our facility. An effective loading and unloading process is ensured.
- SegregateWhen the e-waste reaches the EMPL Facility, the material is tagged and proceeds to data entry. The material is then tested for consistency and then is sent for dismantling.
- Entrepreneurship Every employee should be able to able to pursue their goals and be trained with the state of the art set up.
- Hazardous waste TreatmentHazardous substances recovered during the recycling process are disposed of through a Hazardous Waste Treatment, Storage & Disposal Facility, which is authorized by the Pollution Control Board.
- DismantleFor dismantling, we have a dedicatedspecially designed table in-house, which is equipped with a dust protector and extractor. Next comes the filtration through a HEPA Filter, from where the collected dust will be automatically stored in an attached container that will allow for easy disposal through the TSDF. CRTs, CPUs, Hard Disk SMPS, Printers, Fax machines, ACs, Washing Machines and Lab equipment’s are dismantled separately.
- RecycleNatural Resources, with their limited nature have to be recycled. So, we ensure that as large a portion as possible, of the e-waste that is collected is recycled and the remaining hazardous waste is sent through TSDF.
- Data Crushing / Data DestructionWe value our client’s concerns over data security and it is of the utmost importance to us. We offer many options when it come to the process, some of the options include, degaussing, hard disk drilling alongside dismantling and manual destruction.
- Asset TrackingClients can track the whereabouts of their e-waste and status of disposal through a web-based “Asset-Tracking Tool”. This tool is easy to use and keeps the client up to date on the status of their assigned task.
Disk overwriting to protect confidential information is performed using utilities that securely overwrite information over the hard drive, destroy all partitions, and unused disk space to ensure that all hard drives have been successfully “wiped” in accordance with our strict data security standards.
All equipment are stripped of all identification tags, names, property tags or any symbols identifying the unit to the original owner.
All equipment deemed unusable is recycled in an environmentally sound manner in accordance to our 100% No Landfill Policy. Any hard drives in unusable equipment are physically drilled before being recycled.
We have Strict export policies that ensure no end of life materials intended for disposal is sent to a developing country for disposal. All dismantling is carried out in our facilities and materials are recycled using accredited channels.
Downstream auditing. Traceability and downstream materials movement is the key components of our program. This means pound-for-pound accounting at every level of the recycling process, 100 percent of the time.
With our comprehensive reporting structure we provide a certificate of destruction that includes the total number of items collected, the total weight of the items, materials recovered from the recycling process, percentage of materials in weight diverted from the landfill and number of items that had Data cleansing performed.



